I agree with Buzz Anderson: “Paste-with-styling is one of the worst software inventions of all time.” Every time I mention the workaround shown below, there are many retweets and favorites. Clearly, there are a lot of people that feel the same as Buzz and me.
The solution is surprisingly simple: make Paste and Match Style the default for pasting by mapping the menu item to the ⌘V keyboard shortcut:
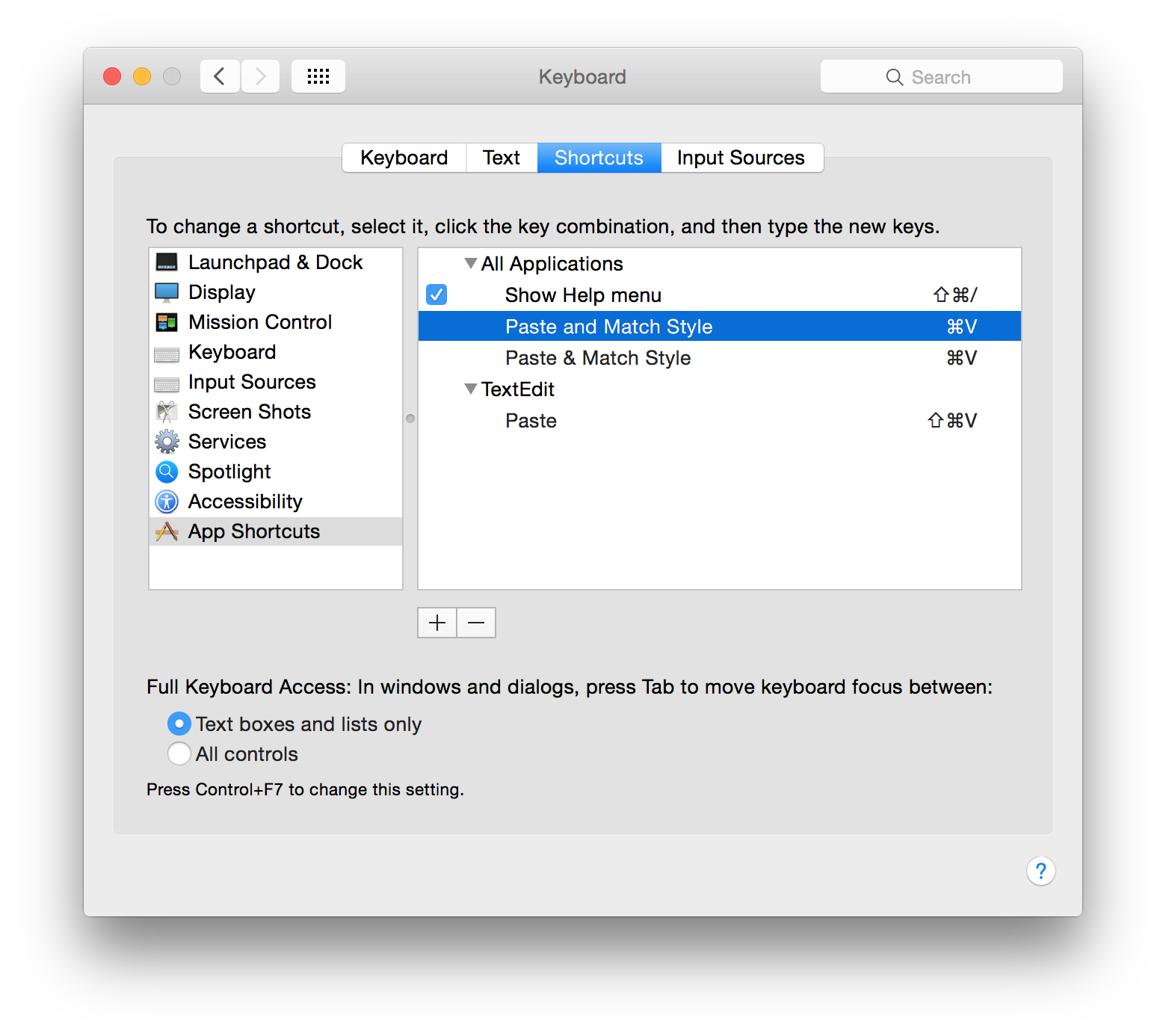
These settings are available in the System Preferences > Keyboard > Shortcuts > App Shortcuts panel. Count the number of clicks required to get to that screen and it should be clear why so many people don’t know about this trick. Another reason for the confusion is that “and Match Style” really means “Without Style”.
You’ll also note that that I have Paste & Match Style mapped. I use some older apps which have an ampersand in the menu item instead of the word “and”. Since app shortcuts work by matching text exactly, this duplicate is needed.
After you’ve made this change, you might find that the keyboard shortcut sometimes doesn’t work. The one that gets me the most is when I try to ⌘V in the “To:” field while composing a message in Mail. When you try to use the shortcut, you’ll hear a beep because the control doesn’t accept styled text and Paste and Match Style is disabled. When this happens, it’s easy enough to right-click and use the context menu or select Paste from the menu bar.
There are some apps where I do want a keyboard shortcut for pasting styled text. The screenshot above shows one: TextEdit. Most of the time I’ll rely on ⌘V to paste text without styling, but if I do want to keep the text’s attributes, ⇧⌘V is just a keystroke away.
If you’ve found this trick useful, be sure to share it. There are a lot of people who don’t know how simple it is to fix this little annoyance.
